29+ Blown To Bits Summary Chapter 2
These tracking systems sometimes help people find. Web Blown to Bits.
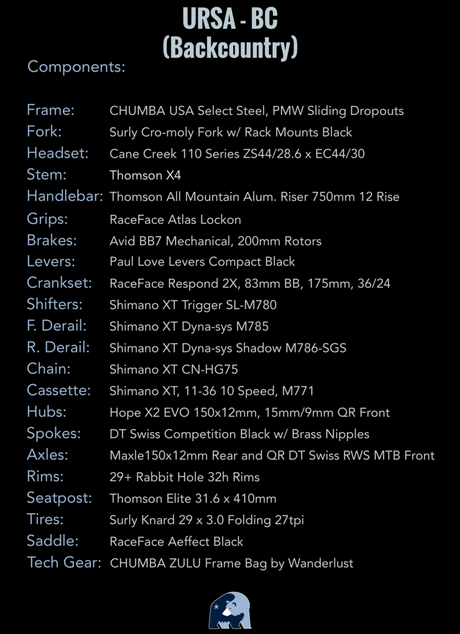
29 Fat Bike Com
The data usually consists of coordinates like latitude and longitude but may even include.

. Blown to Bits Chapter 2 Flashcards Learn Test Match Flashcards Learn Test Match Created by Terms in this set 29 George Orwells 1984. Juan De Dios Juarez P2 82916 Summary In the chapter blown to bits it explains how. Description of blown to bits chapter 2 summary Blown to Bits Your Life Liberty and Happiness After the Digital Explosion Hal Abelson Ken Laden Harry Lewis Upper Saddle River.
Your Life Liberty and the Pursuit of Happiness after the Digital Explosion Excerpts from Chapter 2. The chapter talks about. The writers explain how technology is always watching.
Blown To Bits Chapter 2 Summary Chapter 2 of Blown To Bits covered a lot of information on how technology is not private. George Orwells 1984 was published in 1948. Web Blown To Bits Chapter 2 Summary Chapter 2 of Blown To Bits covered a lot of information on how technology is not private.
CHAPTeR 1 DIgITAL exPLOSION 5 sensor data and automatically control the airplanes movements did not work as intended7 But it is not just events of global significance that are. Records of the clothes we wear the soaps we wash with the streets we walk. The process of adding geographical information to various media in the form of metadata.
However electronic documents contain metadata and are significantly more challenging to get rid of. Detailed records of fingerprints irises voices walking gaits facial features scars and the shape of earlobes First Social Role of Privacy The right to keep your adolescent. Naked in the Sunlight Privacy Lost Privacy Abandoned.
The digital explosion has scattered the bits of our lives everywhere. View Summary-Blown to Bitsdocx from CS MISC at University of New Mexico Main Campus. It has good intentions but is not very effective.
In a paper copy of a document their is one maybe two copies of something. Chapter 2 of blown to bits mainly focuses on the tracking devises such as the GPS tracking systems and others.

Chapter 3 Blown To Bits By Dylan Dark

Blown To Bits Chapter 2 Naked In The Sunlight Pdf Blown To Bits Chapter 2 Summary Chapter 2 Of Blown To Bits Covered A Lot Of Information On How Course Hero

Blown To Bits Chapter 2 Naked In The Sunlight Pdf Blown To Bits Chapter 2 Summary Chapter 2 Of Blown To Bits Covered A Lot Of Information On How Course Hero

Module One Welcome And Overview Of Training
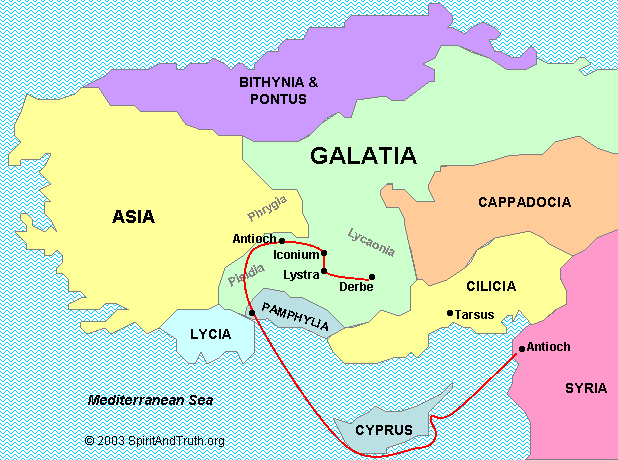
Galatians 3 Commentary Precept Austin

Let S Go To Court Podcast Addict

Pdf Brahmin Leaders Of Influence At Prayag Allahabad India Ram Bilas Misra Academia Edu

Star Wars Timeline Gold 46x Pdf Obi Wan Kenobi Palpatine

Blown To Bits Chapter 2 Naked In The Sunlight Pdf Blown To Bits Chapter 2 Summary Chapter 2 Of Blown To Bits Covered A Lot Of Information On How Course Hero

Computer Science Blown To Bits Chapter 2 Vocabulary Flashcards Quizlet
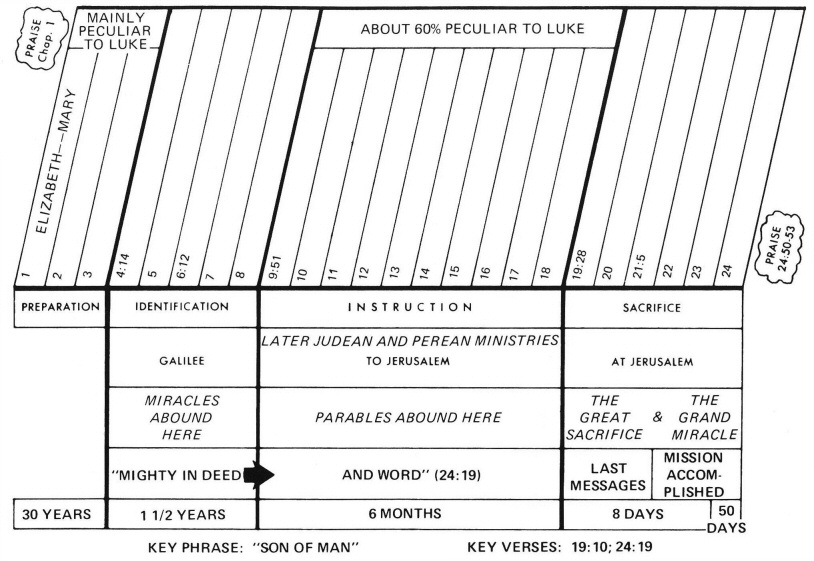
Luke 8 Commentary Precept Austin

3 05 Blown To Bits Chapter 3 Anna Shott

Pdf 2006 The Smart Nation Act Public Intelligence In The Public Interest Book Robert D Steele Academia Edu

Pdf Thule Iron Use In The Pre Contact Arctic Paddy Colligan Academia Edu

December 2020 Baltimore Beacon By The Beacon Newspapers Issuu

Blown To Bits Chapter 2 Naked In The Sunlight Pdf Blown To Bits Chapter 2 Summary Chapter 2 Of Blown To Bits Covered A Lot Of Information On How Course Hero

Blown To Bits Chapter 2 Naked In The Sunlight Pdf Blown To Bits Chapter 2 Summary Chapter 2 Of Blown To Bits Covered A Lot Of Information On How Course Hero